Imprivata MDA Authentication and Single Sign–on Workflows
Imprivata Mobile Device Access extends Imprivata authentication management and single sign–on to mobile devices and apps.
Imprivata MDA supports the following authentication methods:
| Primary Factor | Secondary Factor | Description |
|---|---|---|
| NFC enabled proximity card | (optional) Imprivata PIN or password |
This is the default configuration. In this configuration:
For additional details see, Workflow — Proximity Card with a Second Factor |
| Username and password + (alternative) Imprivata PIN | None |
This configuration supports deployments where proximity cards are not in use. In this configuration:
For additional details, see Workflow — Username/Password + an Alternative Imprivata PIN |
| External proximity card reader | (optional) Imprivata PIN or password |
Certain Android devices don't support NFC; as an alternate method, Imprivata MDA supports the use of certain models of Imprivata-branded rf Ideas external USB proximity card readers. See External Proximity Card Readers In this configuration:
For additional details see, Workflow — Proximity Card with a Second Factor |
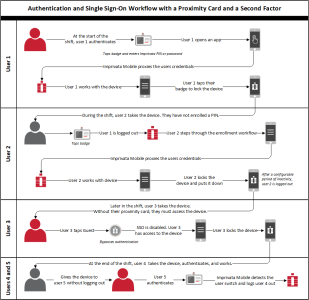
Workflow — Proximity Card with a Second Factor
As illustrated in the following diagram:
-
Users authenticate by tapping their proximity card, and optionally, entering their password or an Imprivata PIN as a second factor.
-
During a specified grace period, all subsequent authentications require a badge tap only.
-
Users can enroll a proximity card and an Imprivata PIN from either the mobile device or the Imprivata enrollment utility on a Windows workstation.
Imprivata MDA steps users through the enrollment when a new proximity card is detected or a PIN is not enrolled.
Click to enlarge.
The diagram includes optional functionality, which you configure in the mobile policy.
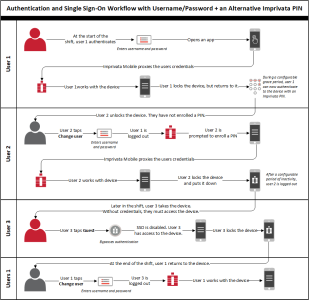
Workflow — Username/Password + an Alternative Imprivata PIN
As illustrated in the following diagram:
-
Users authenticate by entering their username and password.
-
During a specified grace period, an Imprivata PIN can be used for subsequent authentications.
The alternative method can be used until another user authenticates to the device or enters Guest mode.
-
Users can enroll an Imprivata PIN from either the mobile device or the Imprivata enrollment utility on a Windows workstation.
Imprivata MDA steps users through the enrollment if a PIN is not enrolled.
Click to enlarge.
The diagram includes optional functionality, which you configure in the mobile policy.