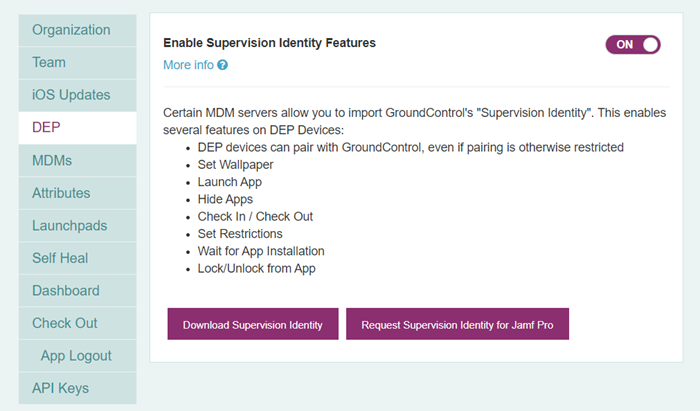
About DEP Supervision Identities
The Supervision Identity allows pairing with your iOS devices, even if the MDM DEP profile assigned to your devices does not allow pairing with other hosts. The option effectively secures devices while retaining management capabilities with Mobile Access Management.
The Supervision Identity is unique to your organization in Mobile Access Management. We export only the “public” component of the supervision; the private key is kept encrypted and is not exportable. Also, Mobile Access Management stores its pairing information in a private database. So this operation to permit pairing to Mobile Access Management does not allow other apps on the same host — such as iTunes, Configurator, etc. — to manage the device.
As always, changes to DEP profiles only can affect devices during activation. Therefore already-activated devices will need to be erased and re-activated to receive these settings. This is unfortunate, but it is a limitation of DEP.
The process below will pre-load Mobile Access Management’s identity to your devices during DEP activation. The identity allows Mobile Access Management to do more with your DEP devices:
-
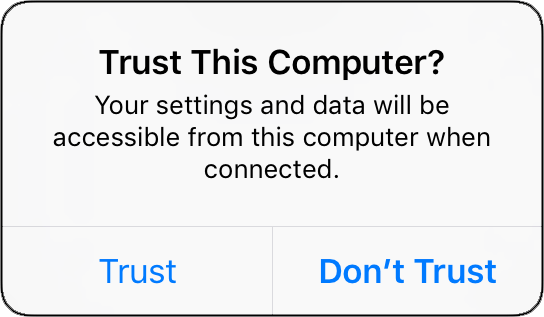
Avoid the “Trust this Computer?” prompt; instead devices pair automatically with any Launchpad app for your organization, even if your DEP profile prohibits pairing
-
Set Wallpaper
-
Launch Apps
-
Hide Apps
-
Check In / Check Out
-
Set Restrictions
-
Wait for App Installation
-
Lock or unlock from App
-
Restore a backup, including system settings, if you follow special instructions
-
Removes the “Unpaired. Please reconnect.” status message.
Specific instructions for various MDM systems are included below.
Step 1: Export the Supervision Identity
In the MAM admin console, navigate to Admin > DEP. Then click on the link to download your supervision identity.
Click to enlarge
Mobile Access Management will save a cryptographic file in .crt format. Keep this file for the next step.
Step 2: Import the identity into your MDM
The tasks you perform depend on your MDM.
-
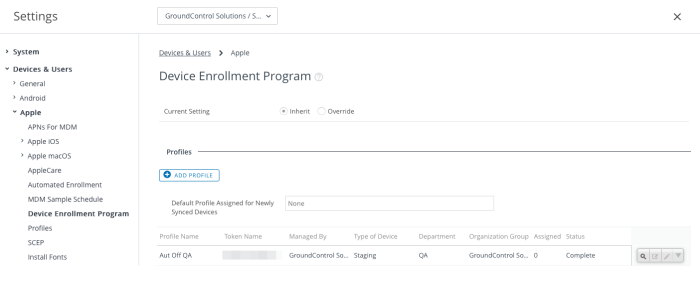
Log into the Workspace ONE Console and ensure you are viewing the correct organization group. Visit Devices > Devices Settings > Apple > Device Enrollment Program. One or more DEP profiles are listed.
-
Edit the profile which will receive the supervision identity.
-
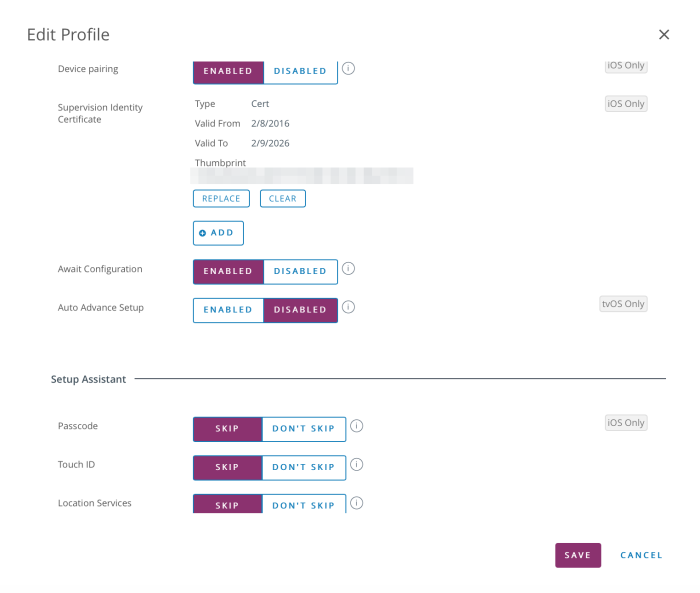
Scroll down to the option for Device pairing. Decide whether you want pairing enabled or not.
-
Click Add and upload the supervision identity file you downloaded from Mobile Access Management in step 1.
-
Save the profile and exit settings.
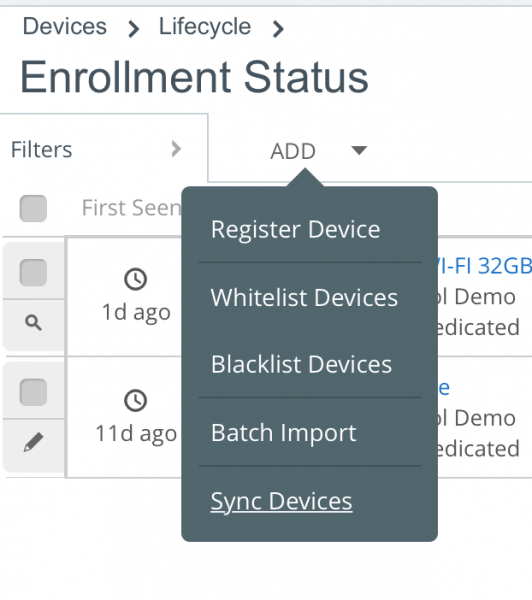
Imprivata recommends that you re-sync with Apple to ensure Apple has the updated profile. Go to Devices > Lifecycle > Enrollment Status, then click Add > Sync Devices.
The supervision identify for Jamf Pro cannot be exported from the MAM console. Contact Imprivata Support to obtain it.
-
After you’ve obtained the supervision identity, log in into the Jamf Pro console and navigate to gear icon on upper right hand corner to access All Settings.
-
Select Device Management > Apple Configurator Enrollment.

-
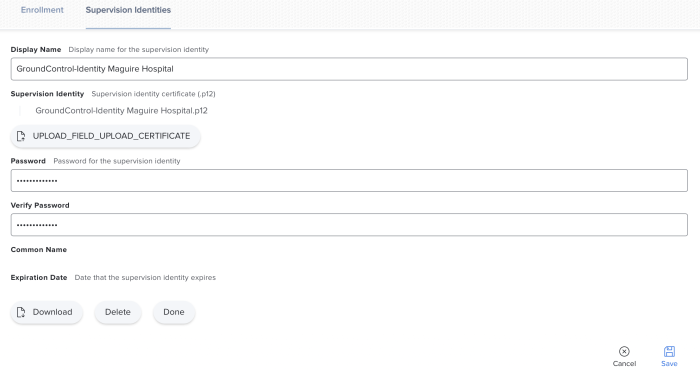
Under Supervision Identities, click Edit , then Upload. Upload the .p12 file provided by Imprivata support.
-
After the file is uploaded, enter the password provided by Imprivata support and click Done, then Save.
-
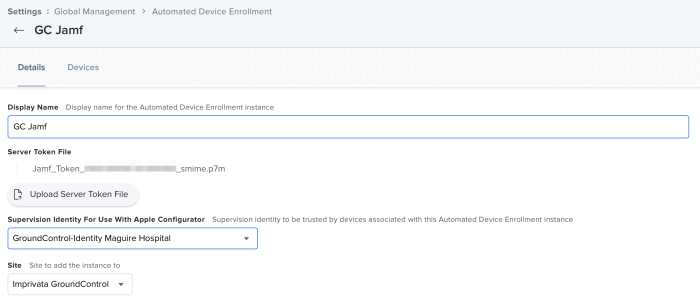
From within Settings, go to Global Management > Automated Device Enrollments and select your device enrollment instance. Click to Edit.
-
Select the Supervision Identity and click Save.
-
If have more than one instance or site, Navigate to PreStage enrollments and ensure the PreStage enrollment with the applicable instance/site is assigned to the devices that will be used with Mobile Access Management.
NOTE:Imprivata strongly recommends creating a new PreStage enrollment configuration to avoid issues with supervision identity association.
-
In InTune, navigate to Device enrollment > Apple Enrollment > Enrollment Program Tokens > Token.
-
Select your DEP profile, and click Properties > Configure Settings > Sync with computer > select Allow Apple Configurator by Certificate > Upload Certificates.
-
Upload your DEP supervisions identity from Mobile Access Management.
IMPORTANT:You may need to rename the identity file’s extension from .CRT to .CER.
-
In the Ivanti Endpoint Manager Mobile admin console, click on Devices & Users > Apple DEP to list your DEP connections (most organizations will have only one).
-
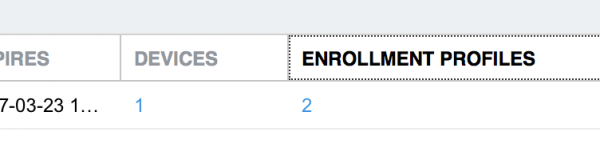
Now list the enrollment profiles by clicking on the number under the column Enrollment Profiles.
-
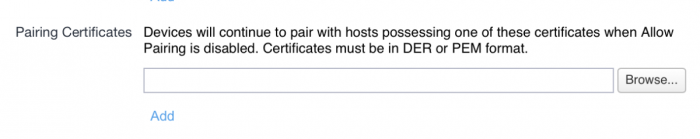
Edit the desired enrollment profile. At the bottom of the dialog is a section on Pairing Certificates.
-
Upload the .p12 supervision identity you downloaded in Step 1. Save the profile.
Imprivata recommends that you re-sync with Apple to ensure Apple has the updated profile. Go to Devices & Users > Apple DEP, then click Check for Updates.
-
In the Ivanti Neurons console, go to Admin > Device Enrollment Program. This lists the DEP connections (most organization have only one).
-
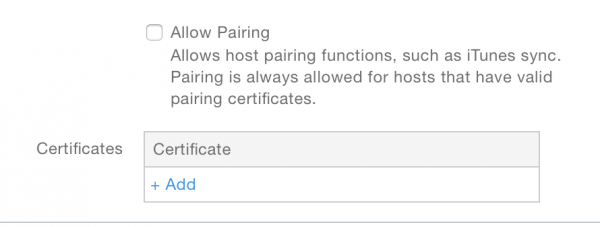
Click Actions > Edit DEP Profile. Scroll down to the Certificates section.
-
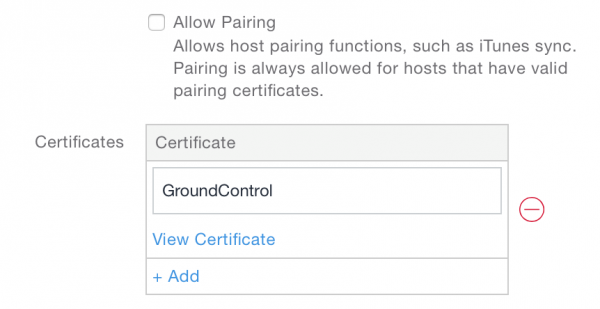
Add the .p12 supervision identity you downloaded in Step 1. You may give the identity any name you wish.
-
Save the profile.
Step 3: Test Pairing
Pairing records are remembered by the host, and survive device erasures. Testing can easily be contaminated by old data. Follow these steps to make sure you are testing correctly.
Test A (Single Launchpad)
-
Erase a DEP device and configure it by hand, without using Mobile Access Management. This ensures Mobile Access Management does not grab the pairing record from the erased device.
-
On your Launchpad choose Reset Launchpad from the File menu (Windows) or Launchpad menu (Mac). This will remove any saved pairing records from that Launchpad. Register the Launchpad when prompted.
-
Pug in the device to the host. After a few moments, you should see the device show up as “DEP, Limited operations available.” You should not see the trust prompt on the device. This means that Mobile Access Management has successfully paired with the device, without additional prompts.
Test B (Multiple Launchpads)
-
Begin by resetting the Launchpads on at least two computers. Then register both Launchpads and have the software running.
-
On computer 1, deploy a DEP-enabled Mobile Access Management workflow to one device. Make sure the device is past all setup screens for the next step.
-
Plug the configured device into the second computer. After a few moments, you should see the device show up as “DEP, Limited operations available.” You should not see the trust prompt on the device. This means that Mobile Access Management has successfully paired with the device, without additional prompts
Notes
These steps are not required for non-DEP (“Manage with Mobile Access Management”) deployments.